
As malware threats evolve to increasingly target Linux systems, admins and organizations must stay up-to-date on the latest Linux malware variants and strategies for detecting and preventing attacks. Security researcher HaxRob recently discovered a new Linux variant of the FASTCash malware, which targets payment switches to enable unauthorized ATM withdrawals.
To help you proactively prepare for this emerging threat, I'll explain the intricacies and targets of this stealthy malware variant and offer advice for detection and prevention. After all, when it comes to malware threats, an ounce of prevention is worth a pound of cure!
Understanding FASTCash Linux Malware
 FASTCash malware, commonly associated with North Korean threat actors such as Lazarus Group, delivers its payload by targeting payment switch systems. ATM and PoS networks use these systems as critical infrastructure components. By exploiting their vulnerabilities, attackers can manipulate transaction messages that enable unauthorized cash withdrawals at ATMs.
FASTCash malware, commonly associated with North Korean threat actors such as Lazarus Group, delivers its payload by targeting payment switch systems. ATM and PoS networks use these systems as critical infrastructure components. By exploiting their vulnerabilities, attackers can manipulate transaction messages that enable unauthorized cash withdrawals at ATMs.
FASTCash has long targeted other operating systems, such as IBM AIX (referred to as FASTCash for UNIX) and Microsoft Windows. However, its discovery on Linux suggests an expansion in the capabilities of cybercriminals, opening up more targets while making defense against attacks more complex.
How FASTCash Linux Malware Operates
A recently identified Linux variant of FASTCash was discovered targeting payment switches running Ubuntu 20.04. Analysis has indicated that this malware was developed post-April 21, 2022, likely using virtualization technology like VMware hypervisor. While similar in function to its Windows counterpart, FASTCash's Linux counterpart offers slightly reduced capabilities yet retains key elements like intercepting and manipulating declined transaction messages.
FASTCash malware, specifically the Linux variant, offers three key capabilities to its victims: transaction interception, fraudulent authorization, and currency manipulation. This malware targets user-space processes on payment switch servers to intercept messages relating to declined transactions for cardholder account numbers on a predefined list. By altering these intercepted messages, FASTCash can authorize transactions that should ordinarily be declined with random amounts of funds involved. Like its Windows variant, it mainly uses the Turkish Lira for currency manipulation efforts.
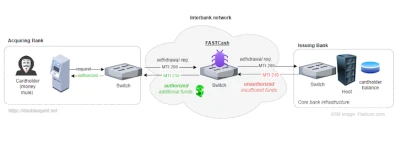 FASTCash Linux Malware Operations (source: doubleagent.net)
FASTCash Linux Malware Operations (source: doubleagent.net)
FASTCash Target Profile
FASTCash malware attacks typically target banks and financial institutions, specifically those operating payment switch systems as targets of attack. Since payment switch systems serve as central hubs for routing and processing transaction flows, compromising them enables attackers to gain control of numerous transactions with significant financial gains for themselves.
Banks hosting their switch applications on Linux servers have been attacked by malware that previously targeted Windows or Unix-based systems. The emphasis on interbank networks suggests an even broader attack against banking infrastructures.
Strategies for Detecting FASTCash Malware
Due to its complex and stealthy nature, FASTCash malware detection requires a multi-pronged approach. Effective strategies include network traffic monitoring, file integrity monitoring, and behavioral analysis. Network traffic monitoring involves suspicious transactions using specific currencies like the Turkish Lira and any unusual communication from payment switch servers to external destinations or command-and-control (C2) infrastructures. File integrity monitoring must focus on verifying checksums of critical software components on payment switch servers to detect unauthorized modifications and provide detailed audit logging of directories and files involved with transaction processing. Behavior analysis involves continuously monitoring running processes to detect unusual activities or resource consumption patterns indicative of malware and inspecting transaction logs for signs of tampering or fraudulent approval of transactions that are usually declined.
Prevention Measures for Admins & Organizations
 Protecting against FASTCash Linux malware attacks involves simultaneously strengthening technological defenses and operational practices. Infrastructure hardening is essential. This includes ensuring that all software running on servers, such as payment switches, is up-to-date to prevent vulnerabilities and adhering to the principle of least privilege by restricting users' and services' access rights. Network segmentation is integral in keeping payment switch systems safe from general network traffic by isolating them behind strong firewalls and creating a Demilitarized Zone (DMZ) to limit direct access to internal servers. Multi-factor authentication (MFA) should be implemented to access critical systems, particularly those involving administrative privileges on payment switch servers. Regular security audits, comprising comprehensive assessments and penetration tests, can assist in identifying potential vulnerabilities to ensure compliance with pertinent financial regulations and cybersecurity standards. Training employees on cybersecurity awareness is also of utmost importance. Teaching staff members how to recognize phishing attempts and other social engineering tactics that could compromise systems and protocols is essential in preventing cyberattacks and breaches.
Protecting against FASTCash Linux malware attacks involves simultaneously strengthening technological defenses and operational practices. Infrastructure hardening is essential. This includes ensuring that all software running on servers, such as payment switches, is up-to-date to prevent vulnerabilities and adhering to the principle of least privilege by restricting users' and services' access rights. Network segmentation is integral in keeping payment switch systems safe from general network traffic by isolating them behind strong firewalls and creating a Demilitarized Zone (DMZ) to limit direct access to internal servers. Multi-factor authentication (MFA) should be implemented to access critical systems, particularly those involving administrative privileges on payment switch servers. Regular security audits, comprising comprehensive assessments and penetration tests, can assist in identifying potential vulnerabilities to ensure compliance with pertinent financial regulations and cybersecurity standards. Training employees on cybersecurity awareness is also of utmost importance. Teaching staff members how to recognize phishing attempts and other social engineering tactics that could compromise systems and protocols is essential in preventing cyberattacks and breaches.
Our Final Thoughts on Combating the Emerging FASTCash Linux Malware Variant
The presence of a Linux variant of FASTCash malware marks an exponential escalation in cybercrime against financial institutions. By understanding its operating mechanisms and developing effective detection and prevention strategies against this new threat, organizations can strengthen their defenses against it and other sophisticated attacks. As with all cybersecurity challenges, being informed, vigilant, and proactive will allow organizations to reduce the risks this formidable adversary presents.

















