
Security researchers have discovered a sophisticated strain of malware targeting Linux servers dubbed Perfctl. Its dual purpose is mining cryptocurrency and proxyjacking.
This malware exploits vulnerabilities while operating stealthily to avoid detection mechanisms, posing a significant risk to organizations relying on Linux-based infrastructures. In this article, I'll help you understand this threat, determine if you are at risk, and share advice for detecting and preventing infections. Let's begin by examining this malware and how it works.
Understanding Perfctl Malware
Perfctl malware has proven itself elusive and persistent over the years. Aqua Security researchers Assaf Morag and Idan Revivo state that its primary objective is running cryptocurrency mining and proxyjacking software on compromised Linux servers. Aqua Security researchers reported that Perfctl employs various sophisticated techniques to stay undetected while remaining persistent on infected machines.
When Perfctl infiltrates a server, all resource-intensive activities immediately cease when a new user logs on. It is dormant until server traffic subsides again, thus avoiding detection by humans checking performance metrics periodically. When executed, Perfctl deletes its binary to cover its tracks before continuing as an invisible background service.
The Attack Chain
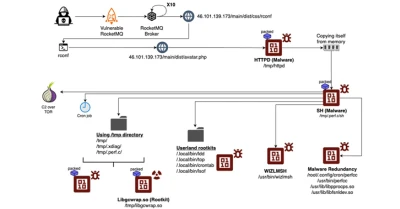 Perfctl Attack Chain (Source: Aqua Nautilus)Perfctl employs an effective and innovative attack chain. After exploiting a vulnerable Apache RocketMQ instance to deliver an initial payload known as "httpd," execution of this payload copies itself into the "/tmp" directory, launches another binary process, and deletes itself to mask its presence and avoid detection. Hence, its presence remains obscured until detection occurs later on.
Perfctl Attack Chain (Source: Aqua Nautilus)Perfctl employs an effective and innovative attack chain. After exploiting a vulnerable Apache RocketMQ instance to deliver an initial payload known as "httpd," execution of this payload copies itself into the "/tmp" directory, launches another binary process, and deletes itself to mask its presence and avoid detection. Hence, its presence remains obscured until detection occurs later on.
Perfctl takes advantage of a security flaw in Polkit (CVE-2021-4043 or PwnKit) to gain root privileges and use them to deploy its primary payload: a cryptocurrency miner named perfcc and rootkit protection against defense evasion. Some instances also download and execute proxyjacking software from remote servers, highlighting its dual nature.
Evasion Mechanisms
Perfctl uses several sophisticated evasion techniques to avoid detection and removal, including binary deletion. Upon execution, Perfctl deletes its initial binary file immediately - making it hard for security researchers to pinpoint its origin. Perfctl uses a rootkit to hide its processes and activities from system monitors and administrators, as well as fileless attack methods aimed at operating solely within memory, which help avoid traditional file-based antivirus and detection tools. Named "perfctl," the malware's name seeks to appear as a legitimate system process. Perf stands for Linux performance monitoring tool, while "ctl" is often seen in command-line tools like systemctl or timedatectl - giving an appearance of benignness to this dangerous code.
Impact of an Attack
A Perfctl attack can have grave repercussions that wreak havoc on affected systems and organizations, with cryptocurrency mining taking up significant system resources, leading to decreased performance and rising operational costs. Given its root access, malware could use this opportunity to exfiltrate sensitive data from compromised computers - creating severe security risks. Proxyjacking attacks also can take advantage of compromised systems to route malicious traffic and implicate victims in illegal activities. Perfctl's persistence mechanisms can cause extended operational downtime as organizations work to identify and mitigate its infection. Furthermore, for organizations governed by regulatory bodies such as HIPPA/FERPA regulations, successful Perfctl attacks could mean noncompliance with data security regulations - which could lead to severe legal and financial repercussions for noncompliance.
What Countries & Sectors Are Affected by Perfctl?
The Perfctl malware campaign has had a devastating effect on numerous countries and sectors worldwide, most notably in the US, Germany, and South Korea—three countries that heavily rely on Linux servers, particularly within cloud and enterprise environments. As these locations boast high computational demands due to widespread Linux server usage, they have become prime targets of Perfctl crypto mining and proxyjacking activities.
Perfctl has targeted cryptocurrency and NFT platforms and the software development and publishing industries, specifically exploiting server resources for crypto mining purposes without being detected by users. These industries are particularly vulnerable because they often operate within Linux environments with open-source platforms and utilize developer forums and repositories as propagation methods. Hence, there is a need for enhanced cybersecurity measures in these industries to minimize its spread. Let's examine some measures developers and organizations can take to mitigate risk.
Detection and Prevention
 Organizations need to implement comprehensive strategies to detect and prevent Perfctl attacks, which include adopting comprehensive detection tactics. This includes monitoring CPU usage for unexpected spikes or system slowdowns during idle periods, as these can indicate cryptocurrency mining activity, and employing rootkit detection and removal tools as well as network and host-based intrusion detection systems to monitor for abnormal activities and any attempts at unauthorized access.
Organizations need to implement comprehensive strategies to detect and prevent Perfctl attacks, which include adopting comprehensive detection tactics. This includes monitoring CPU usage for unexpected spikes or system slowdowns during idle periods, as these can indicate cryptocurrency mining activity, and employing rootkit detection and removal tools as well as network and host-based intrusion detection systems to monitor for abnormal activities and any attempts at unauthorized access.
Prevention measures are also crucial. Ensuring regular updates and patches for systems and software helps address vulnerabilities like CVE-2021-4043 (PwnKit), which are gateways for malware entering systems. Implementing tight permissions to manage which files and binaries can be executed on the server is essential, as is disabling any services that could expose it to potential vulnerabilities. Network segmentation should be implemented to restrict an attacker's lateral movement within a network. Role-based access control (RBAC) should also be employed so only users who require access can gain entry. These measures will significantly strengthen an organization's resilience against Perfctl threats.
Our Final Thoughts on Combating the Perfctl Malware Threat
Perfctl malware is a testament to the evolving complexity and sophistication of cyber threats targeting Linux servers. Perfctl poses a severe risk to organizations across various sectors by exploiting vulnerabilities while employing advanced evasion techniques. Monitoring system performance closely, updating security patches regularly, restricting file executions, and creating robust access controls are necessary measures against Perfctl attacks. As the digital landscape expands, so must our protection efforts against threats like Perfctl.

















