
Developers recognize the critical nature of protecting software systems as cyberattacks grow more sophisticated, thus necessitating robust security measures in development lifecycle processes. Code security scanners play a vital role here. These tools are intended to detect, mitigate, and prevent security vulnerabilities in code, improving integrity, reliability, and security for software systems.
In this article, I'll delve deeply into the function and importance of code security scanners developed by Google: AddressSanitizer (ASan), MemorySanitizer (MSan), UnknownBehaviorSanitizer (UBSan), Control Flow Integrity (CFI), LibFuzzer, and AFL (American Fuzzy Lop). Let's begin by gaining a deeper understanding of code security scanners and their importance in secure Linux software development.
What Are Code Security Scanners?
Code security scanners are tools used to scan source code to detect potential security flaws and flag them for further review by coders or testing services. Such analyses could involve either static analysis (without running it), dynamic analysis (while running), or some combination thereof. The goal is to identify flaws attackers might exploit, like buffer overflows, race conditions, and injection vulnerabilities.
The Importance of Code Security Scanners in Secure Linux Software Development
 Code security scanners play an essential role in secure development. By integrating them early into their processes, developers can identify and address vulnerabilities before production-ready software reaches distribution, thus decreasing risks associated with security breaches.
Code security scanners play an essential role in secure development. By integrating them early into their processes, developers can identify and address vulnerabilities before production-ready software reaches distribution, thus decreasing risks associated with security breaches.
Proactive security solutions can be cost-efficient and effective. By addressing security issues during development rather than post-release fixes that often involve lengthy patches that compromise an organization's credibility and require extensive costs, organizations can minimize potential negative repercussions while protecting themselves from future liabilities. Many industries impose stringent regulatory standards on software security, and code security scanners can assist by documenting sound security practices and assuring regulatory compliance. Beyond increasing security, code security scanners improve overall software quality by identifying bugs or performance issues that would remain undetected.
Code Security Scanners Developed by Google
Google has developed several security tools that are invaluable for open-source security researchers attempting to quickly detect Type Confusion flaws during code development. Here is an introduction to each of Google's security tools and how they can be utilized:
AddressSanitizer (ASan)
AddressSanitizer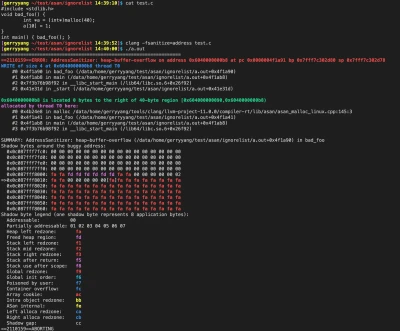 is a memory error detector that identifies issues such as out-of-bounds accesses to heap, stack, and global variables and use-after-free bugs. ASan works by instrumenting code to detect memory errors at runtime, making it a powerful way of discovering buffer overflows or heap corruption issues.
is a memory error detector that identifies issues such as out-of-bounds accesses to heap, stack, and global variables and use-after-free bugs. ASan works by instrumenting code to detect memory errors at runtime, making it a powerful way of discovering buffer overflows or heap corruption issues.
Utilization:
ASan can quickly become part of any development workflow by being activated during compilation. Developers can run their programs with ASan enabled and watch it flag memory errors as they arise, providing complete diagnostic information that facilitates debugging efforts.
MemorySan (MSan)
MSan was developed to detect uninitialized memory reads. This tool detects instances where variables are being used without initializing correctly, potentially leading to unpredictable behavior and security vulnerabilities. MSan instruments code during compilation to monitor reads/writes on memory, so any use of uninitialized memory is promptly flagged as used memory by MSan.
Utilization:
Developers can utilize MSan by compiling their code with MSan instrumentation enabled. Running this instrumented program will allow MSan to identify instances of uninitialized memory usage, helping developers address them before becoming security issues.
UnknownBehaviorSanitizer (UBSan)
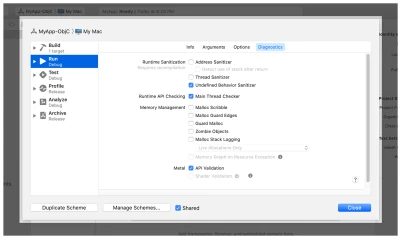 UnknownBehaviorSanitizer (UBSan) targets undefined behavior in code, such as integer overflows, misaligning pointers, and invalid casts, that might not cause immediate crashes but can lead to severe bugs and security vulnerabilities later down the road.
UnknownBehaviorSanitizer (UBSan) targets undefined behavior in code, such as integer overflows, misaligning pointers, and invalid casts, that might not cause immediate crashes but can lead to severe bugs and security vulnerabilities later down the road.
Utilization:
UBSan can be utilized by compiling code with UBSan instrumentation enabled, running it through execution, and monitoring for unanticipated behavior or incidents during run time. Developers can be provided with detailed reports to address these problems proactively.
Control Flow Integrity (CFI)
CFI is a security feature that ensures a program adheres to only legitimate paths defined by its control flow graph, thus protecting itself from attacks such as return-oriented programming (ROP) attacks that might divert its execution path from what was planned by design.
Utilization:
CFI can be implemented by compiling code with support for control flow integrity enabled. Once activated, CFI will check that program execution matches the expected control flow graph, blocking any attempts at malicious manipulation by running continuous verification checks that ensure execution conforms to expected flow charts.
libFuzzer
libFuzzer is a coverage-guided fuzzing tool used with sanitizers like ASan and UBSan to maximize security flaw detection. Fuzzing involves injecting random inputs into programs being tested to uncover hidden bugs by creating unexpected behavior that generates unexpected patterns that result in unforeseen bugs being exposed during testing. Due to these powerful combinations, libFuzzer excels in discovering Type Confusion vulnerabilities.
Utilization:
Developers utilize libFuzzer by writing "fuzz targets," which are particular entry points called by libFuzzer with various inputs. By pairing this approach with other testing sanitizers, developers can uncover hidden vulnerabilities through extensive fuzz testing, ensuring robust software security.
American Fuzzy Lop [AFL]
AFL (American Fuzzy Lop)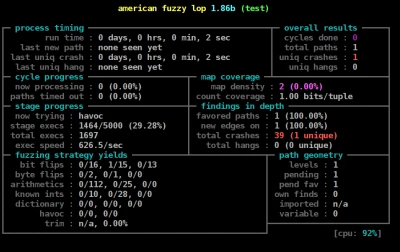 is a security-oriented fuzzer that employs genetic algorithms to automatically discover test cases that cause crashes or expose other potential issues with software applications. AFL tracks the execution path of a tested program while altering inputs to find new code paths, effectively uncovering any security flaws, such as Type Confusion vulnerabilities, that remain concealed under surface code paths.
is a security-oriented fuzzer that employs genetic algorithms to automatically discover test cases that cause crashes or expose other potential issues with software applications. AFL tracks the execution path of a tested program while altering inputs to find new code paths, effectively uncovering any security flaws, such as Type Confusion vulnerabilities, that remain concealed under surface code paths.
Utilization:
Utilizing AFL in testing can be achieved by instrumenting code and running its fuzzer against its binary version, then running AFL's generator/mutate in an automated fashion to simulate inputs/mutations for testing purposes and identify vulnerabilities through comprehensive automated tests.
Integration into the Linux Software Development Workflow
Integrating code security scanners into the development workflow is critical to creating secure codebases. By embedding such tools within Continuous Integration/Continuous Deployment (CI/CD) pipelines, code is continuously tested for vulnerabilities throughout its lifespan and development lifecycle. Educating developers on security scanners' benefits and proper use is paramount for timely detection and resolution. Training sessions and resources may assist developers in integrating this tool smoothly into their daily workflow. At the same time, regular code audits should complement automated scanning tools as human oversight may identify problems missed by automated scanners.
Our Final Thoughts on the Benefits of Code Security Scanners for Secure Linux Software Development
AddressSanitizer, MemorySanitizer, UndefinedBehaviorSanitizer, Control Flow Integrity, libFuzzer, and AFL have become essential tools in developers' toolkits in an ever-evolving Linux security landscape. Developers must ensure that software remains robust, secure, and reliable by including security scanners in development projects. As with anything worth doing, an "ounce of prevention is worth a pound of cure." Security scanners allow developers to address security threats before users experience them directly.















