
Balancing strong security measures while minimizing operational risks is a constant juggling act in cybersecurity. The recent global outage caused by that bad CrowdStrike update underscores the risks of relying on kernel-level modules for security.
In this article, we'll dive into that incident, discuss the dangers of kernel-level security, and look at some examples of Linux rootkits and kernel security modules. Plus, we'll share some handy tips to help Linux administrators prevent such disasters in the future.
What Happened to CrowdStrike’s Kernel Module?
 CrowdStrike released a software update in July 2024 for its Falcon monitoring product. Falcon is a kernel-level security module for Windows, which means it operates extremely deep within the operating system.
CrowdStrike released a software update in July 2024 for its Falcon monitoring product. Falcon is a kernel-level security module for Windows, which means it operates extremely deep within the operating system.
This update was flawed and proved to be disastrous. The bug caused a chain reaction that brought down critical systems worldwide. The compromised systems at airports caused massive delays. Given the nature of their work, you can imagine how terrifying it is for hospitals to experience operational disruptions. Even banks were not spared. This led to financial chaos and downtime.
This incident is a stark reminder of the risks associated with integrating security modules at a deep level. This can have devastating, sweeping effects when something goes wrong on the kernel level. This is a perfect example of the high-stakes game we play regarding cybersecurity. One minor glitch can bring critical infrastructures around the world to a halt. It warns everyone in the tech and security industries about the importance of rigorous testing and careful deployment, especially with something as fundamental as kernel-level software.
Understanding Kernel Drivers
Windows and Linux are built around a component called the "kernel." The kernel is responsible for critical functions, such as managing system resources and controlling hardware operations. The kernel can be modified to support new hardware and functionalities using "drivers." Drivers are usually required for new hardware like GPUs, but they can also perform other functions, such as cybersecurity.
Kernel Level Security Modules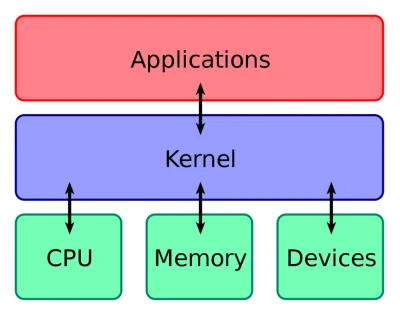
Security software uses Kernel-level drivers to operate at a very low level of the OS. They can monitor and control basic operations like network connections and file access, allowing a comprehensive defense from malware and other cyber threats. However, embedding the security functionality within the kernel poses substantial risks. Unlike typical software bugs, kernel code flaws can cause severe system failures, which may only cause isolated crashes.
What Does This Mean for System Administrators?
The CrowdStrike failure highlights the risks that system administrators face, especially those who manage Linux environments and rely on security integrations at the kernel level. The risks include widespread system instability, complicated recovery processes, cascading failures, and complex recovery procedures. Linux administrators are at greater risk due to the custom kernels they use, their reliance on dependencies from open-source, and the need for careful patch management. This incident highlights the importance of robust testing, progressive updates, and diverse security measures to protect system stability and integrity.
Kernel-level Integration Risks
The risks of kernel-level integrations for system administrators and Linux users cannot be understated. System Stability Kernel drivers have full access to all critical system functions. One bug can cause widespread system failures.
- Recovery Is Complex: Fixing problems often requires manual intervention, such as booting in recovery mode and applying low-level fixes. This can be laborious and time-consuming.
- Cascading Failures: As shown in the CrowdStrike case, kernel-level bugs can cascade failures on interconnected systems, increasing the impact.
Linux Administrators are at Risk
 As a Linux admin, I quickly learned that managing security was a complex challenge. A colleague working as an administrator for a mid-sized company discovered that the network had been compromised by a sophisticated rootkit at the kernel level. The rootkit was undetectable despite the company's strict security protocols, allowing the attacker to steal sensitive customer data over weeks. Only after noticing abnormal network traffic patterns was the breach detected.
As a Linux admin, I quickly learned that managing security was a complex challenge. A colleague working as an administrator for a mid-sized company discovered that the network had been compromised by a sophisticated rootkit at the kernel level. The rootkit was undetectable despite the company's strict security protocols, allowing the attacker to steal sensitive customer data over weeks. Only after noticing abnormal network traffic patterns was the breach detected.
This experience highlighted the specific risks we, as Linux administrators, face. We must always stay on top of the evolving threats. Kernel vulnerabilities can be devastating, giving attackers access to deep and often undetectable information. To ensure that the systems I manage remain as secure as they can be, I no longer just rely on routine patches and updates but also take advanced measures such as implementing robust security modules, performing regular audits, and ensuring continuous monitoring. This story is a constant reminder to remain vigilant and maintain the integrity and safety of Linux environments.
Linux's stability and robustness are often its greatest strengths, but these can be vulnerabilities if kernel-level security modules are involved.
- Customized Kernels: Many Linux systems use kernels tailored to meet specific needs. Third-party kernel drivers may disrupt these carefully tuned systems.
- Open-Source Dependencies: Linux administrators rely on many open-source components that may need to be tested rigorously for compatibility with the latest kernel modules.
- Patch Management: Linux distributions are decentralized, so updates and patches must be managed carefully. This is because they must ensure stability.
Linux Rootkits and Their Effects
In my research into the effects of Linux Rootkits, I've looked at several famous examples that have historically compromised Linux Systems. Adore, Knark, and Phalanx2 are three examples that demonstrate remarkable abilities to conceal malicious activities and avoid detection. Adore, which provided hidden backdoors to intruders, was especially insidious. Knark, on the other hand, manipulated kernel operations to remain undetected. Phalanx2 was notable for its combination of hiding abilities and keylogging, allowing it to steal sensitive data efficiently. These studies have shown rootkits can lead to prolonged unauthorized access and significant data breaches.
Rootkit: Adore (2000)
- Adore is one of the first well-known rootkits available for Linux. It allows an attacker to hide files, processes, and network connections.
- Effect: Administrators discovered hidden backdoors, which compromised the integrity of systems. Adore’s ability to conceal its presence rendered traditional detection methods useless, and many systems were unknowingly exposed to long-term spying.
Rootkit: Knark (2001)
- Knark manipulates the Linux kernel to intercept and control calls. It could hide users, files, processes, and even admin tools from standard admin tools.
- Effect: Infected systems are virtually undetectable, which allows attackers to conduct covert operations like data exfiltration or extended control of the compromised system.
Rootkit: Phalanx2 (2003)
- Phalanx2 has been designed as a sophisticated rootkit to backdoor Linux. It can hide directories, files, and processes and log keystrokes.
- Phalanx2 combined its hiding abilities and keylogging to cause severe data breaches. These included the theft of sensitive credentials and intellectual property, which extended the attacker's ability to control the infected system.
Rootkits: A Parallel Threat
Rootkits are another issue that Linux administrators should be concerned about when it comes to kernel-level integration. These malicious programs insert themselves insidiously into the Linux kernel, avoiding detection and maintaining persistent control over the computer.
Rootkits: How Do They Work?
Rootkits can hide their presence by altering core operating system components:
Rootkits can hide themselves by injecting code into the kernel. They can intercept system calls, modify kernel data structures, and evade anti-virus tools.
- File and Process Hider: Rootkits can hide files, directories, and processes, making detection more difficult.
- Keystroke Logging & Credential Theft: Rootkits often include functionality that allows them to steal sensitive information, such as user credentials, data, and other sensitive information, directly from operating systems.
 Rootkits: How Do They Impact Security and Integrity
Rootkits: How Do They Impact Security and Integrity
Rootkits compromise vital components and allow attackers to alter system files or hide from detection mechanisms. This section highlights the potential threats, including data breaches, unauthorized data manipulations, and possible system downtimes. The section also highlights the broader implications of IT environments for trust and reliability. This report highlights the need for proactive measures such as regular audits and advanced detection tools. Comprehensive security protocols are also necessary to reduce these risks. A rootkit is a serious threat to the integrity and security of any system.
- Invisibility: Because rootkits are so low-level, they may be undetectable by traditional security tools. This allows the attacker to remain undetected in the system for long periods.
- Data Integrity: Rootkits can alter system logs, monitor traffic, and change application behavior, making it difficult to trust data or activities on a compromised machine. They grant attackers root-level privileges, which allows them to take any action they want on the system, including exfiltrating information or deploying more malware.
Examples of Linux Kernel Security Modules
There are several examples of how Linux kernel modules can enhance system security. SELinux and AppArmor are three prominent solutions. SELinux uses mandatory access controls to enforce strict policies. On the other hand, AppArmor uses path-based control to specify file permissions. TOMOYO, on the other hand, focuses more on policy learning to create custom security profiles that are tailored to specific system behavior. In my research, I've learned how these modules collectively strengthen the security of Linux systems by providing robust mechanisms for managing permissions and enforcing security policies.
Module: SELinux (Security-Enhanced Linux)
- Purpose: Designed to provide a robust and flexible Mandatory Access Control (MAC) mechanism for Linux.
- Function: SELinux enforces security policies that limit program and user capabilities, tightly controlling access permissions to reduce the risk of system exploitation.
Module: AppArmor (Application Armor)
- Purpose: Provides a security framework that protects operating systems and applications from external or internal threats.
- Function: AppArmor uses profiles to define permissible actions for applications, preventing them from performing unauthorized actions.
Module: Seccomp (Secure Computing Mode)
- Purpose: Designed to limit the system calls that applications can make, thereby reducing the attack surface.
- Function: Seccomp is used to sandbox programs by allowing them to execute only a specific subset of system calls, making it harder for attackers to exploit vulnerabilities within those applications.
Kernel Security Issues: How Can I Reduce Risk?
Kernel-level security issues can pose significant risks to your Linux systems, making it crucial to have a strong defense strategy. As a Linux admin, you know these vulnerabilities can lead to severe consequences, including system breaches and data loss. This guide provides practical recommendations to help you mitigate these risks and protect your systems from potential rootkit threats. Let's dive into some essential steps you can take to fortify your kernel security.
Secure Your Policies
Establish and enforce sound security policies based on the principle of least privilege. Access to critical resources should only be granted on a need-to-know basis. Regularly review and update your policies to stay on top of new threats.
Stay up to date with the latest updates.
It is essential to keep your system updated. Developers patch kernel vulnerabilities regularly, so you want to keep your system safe. Automate updates whenever possible and create a bulletproof process for emergency patches.
Use Advanced Security Modules
Frameworks such as SELinux and AppArmor can boost your system's safety. These advanced modules enforce strict access controls, making breaches harder to commit. Make sure they are configured correctly and monitored.
Real-Time Monitoring and Auditing
Continuous monitoring and auditing will help you monitor your system's activities. Tools such as an Intrusion Detection System (IDS) and security Information and Event Management (SIEM) are used to detect suspicious behavior before it becomes a problem.
Layer your security measures.
Adopt a defense-in-depth strategy, layering several security controls to avoid a single failure point. When one security measure fails, other measures can keep your system safe.
Perform Regular Security Audits
Conduct security audits and risk assessments regularly to detect potential vulnerabilities. Third-party security experts provide unbiased views and can make actionable suggestions for improving your defenses. Use rootkit scanners to detect possible exploits.
Containerization and Virtualization
Virtualization and containerization are great ways to separate workloads. By isolating services and applications, you can reduce the risk that a single security breach will compromise your entire system.
Keep in touch with the Security Community.
Engage with the cybersecurity community to stay informed about the latest threats. Participate in forums, open-source projects, and security conferences for insights and to keep up with possible risks.
Follow these guidelines to reduce the risk of rootkits. Layered, comprehensive security will make your system resilient and ready for anything.
Keep Learning about Rootkits and Kernel Security Modules
 CrowdStrike poignantly reminds us of the dangers of relying solely on kernel-level modules for security. Rootkits are a parallel threat, highlighting the need to be cautious when extending the kernel. Kernel-level security provides unparalleled control and access, but the possibility of catastrophic failures should something go wrong requires a balanced approach. Linux administrators must be vigilant due to the OS's decentralized nature and customization ability.
CrowdStrike poignantly reminds us of the dangers of relying solely on kernel-level modules for security. Rootkits are a parallel threat, highlighting the need to be cautious when extending the kernel. Kernel-level security provides unparalleled control and access, but the possibility of catastrophic failures should something go wrong requires a balanced approach. Linux administrators must be vigilant due to the OS's decentralized nature and customization ability.
Organizations can improve their security posture by implementing rigorous tests, adopting phased deployment strategies, leveraging diverse tools, maintaining robust recovery protocols, and being vigilant about rootkits. The ultimate goal is to build a flexible and resilient security framework capable of coping with the threats it was designed to counter and the vulnerabilities it might inadvertently introduce.
















