
At a time when security breaches have become increasingly sophisticated, an oversight that had persisted across major browsers for years has now been addressed. This critical security update protects personal and enterprise digital spaces against an obscure vulnerability: the 0.0.0.0 IPv4 address.
This vulnerability highlights the stealth of cyber threats and the critical importance of adaptive security measures in combating them. I'll explain this vulnerability, its impact, and the community's response and provide insight into what we can learn from it.
Understanding the 0.0.0.0 Day Vulnerability
Oligo Security recently discovered and patched an alarming security loophole that enabled malicious web pages to request IPv4 address "0.0.0.0", giving attackers access to services ordinarily inaccessible from outside, even behind firewalls, and considered secure. They labeled this oversight the "0.0.0.0 Day" due to its long duration without being appropriately addressed.
This vulnerability impacts browsers like Google Chrome, Microsoft Edge, Firefox, and Safari, which run on MacOS and Linux systems. According to reports, attackers have exploited this flaw since at least the late 2000s, with threads discussing similar issues dating back then.
Impact and Exploitation
 Exploiting this flaw is shockingly straightforward: when users visit malicious webpages, their requests are routed directly to 0.0.0.0 at the port number given, potentially revealing sensitive data or permitting unintended interactions between services that should be protected against external access and the Internet.
Exploiting this flaw is shockingly straightforward: when users visit malicious webpages, their requests are routed directly to 0.0.0.0 at the port number given, potentially revealing sensitive data or permitting unintended interactions between services that should be protected against external access and the Internet.
Even though its chances for actual exploitation may seem remote, vulnerability remains an inherent risk in any local service system. Many believe their local services are safe from external threats, but in actuality, they must take measures to secure them against external attacks.
Response and Mitigations
After discovering this bug, browser developers quickly responded. Chromium-based browsers like Google Chrome, Microsoft Edge, WebKit-based Safari, and Mozilla's Firefox are all pledged solutions. Chrome promises to block access to 0.0.0.0 starting with Chromium version 128 and complete implementation by version 133.
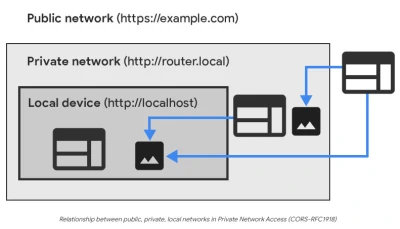 Private Network Access (PNA) [Source: https://developer.chrome.com/blog/private-network-access-update ]Safari has modified its WebKit engine to block access, while Mozilla altered its Fetch specification to stop exploits of this kind. While these browser-based fixes are key, they signal the need for standardization in protecting local networks against web threats.
Private Network Access (PNA) [Source: https://developer.chrome.com/blog/private-network-access-update ]Safari has modified its WebKit engine to block access, while Mozilla altered its Fetch specification to stop exploits of this kind. While these browser-based fixes are key, they signal the need for standardization in protecting local networks against web threats.
Cross-Origin Resource Sharing (CORS) and Private Network Access (PNA) were meant to protect against this vulnerability by restricting web pages from reaching private networks or local services. Unfortunately, the 0.0.0.0 Day exploit managed to circumvent them and exploit local network access.
Oligo Security's research underscores the necessity for more robust standards like PNA to be widely adopted and properly implemented across browsers and web services. This incident is a stark reminder of cyber threats' ever-evolving nature and requires us to advance defenses against them constantly.
Practical Takeaways & Recommendations
 Businesses and individual users should view this vulnerability as an alert that reminds them to reevaluate their digital security posture, specifically surrounding local services that can be accessed over the web. Below are some steps they can take to increase protection from similar vulnerabilities:
Businesses and individual users should view this vulnerability as an alert that reminds them to reevaluate their digital security posture, specifically surrounding local services that can be accessed over the web. Below are some steps they can take to increase protection from similar vulnerabilities:
- Stay Current With Web Browser Updates: Staying current with web browser updates will allow you to take advantage of security patches and improvements as soon as they become available.
- Audit Local Services: Regularly assess any services running locally on devices for their necessity and potential risks.
- Implement Network Segmentation: Where possible, segment networks to isolate sensitive services and ensure additional layers of isolation for them.
- Educate and Inform Users: Users and teams should be aware of any risks associated with local services and encouraged to practice safe browsing habits to protect themselves.
Our Final Thoughts: What Can We Learn from This Flaw?
The patching of the 0.0.0.0 Day vulnerability in virtually all major web browsers marks an essential achievement in the ongoing fight against digital threats while reminding us of their complexity and ever-evolving nature. By learning from such oversights, digital communities can further fortify their defenses and ensure a safer cyberspace.
Preventing similar vulnerabilities requires an ongoing partnership among developers, users, and security professionals - with all parties working to improve digital security against attackers' ingenuity. Staying one step ahead in this digital cat-and-mouse game through continued vigilance, cooperation, and innovation is essential.


















